1. Good Monday Morning
It’s December 20th. Spotlight is off next week and back on January 3. We wish joy, happiness, and a wonderful holiday to everyone celebrating.
Today’s Spotlight is 1,446 words — about a 5 minute read.
2. News To Know Now
Quoted:“CISA also strongly urges every organization large and small to follow the federal government’s lead and take similar steps to assess their network security and adapt the mitigation measures outlined in our Emergency Directive. If you are using a vulnerable product on your network, you should consider your door wide open to any number of threats,” — Jen Easterly, U.S. Cybersecurity and Infrastructure Security Agency Director
a) Family location app Life360 is reportedly sharing locations with more than just parents. The Markup is reporting that the software company that sells the app is also selling location data to brokers. Those brokers then package the data and sell it broadly to all sorts of companies. A former employee told The Markup that people who didn’t opt out could have their location data shared within twenty minutes of it being recorded.
b) Amazon is under intense fire after Illinois-based delivery drivers accused the company of threatening their jobs if they stopped deliveries during a tornado alert. Six of their co-workers died when their warehouse workplace was hit by a tornado. Amazon says that local managers did not follow the company’s safety policies.
c) FTC Chair Lina Khan pledged to make data privacy an agency priority in a letter to Sen. Richard Blumenthal (D-CT). Rulemaking that sets national data privacy requirements similar to those in California and Virginia is one of the options being explored.
3. Search Engine News — Local SEO Update & Learning What Works
Besides being physically attractive and very, very smart, search marketers are usually excellent at recommending best practices to improve a website’s visibility in Google and other search engines. Many of us generally know what works, what Google and Bing recommend, and the technical knowledge to tie them all together.
But the best of us will tell you that we can’t divine which element is responsible for a website’s success in search visibility. Google search exec John Mueller cut through the hyperbole last Wednesday when he answered a question this way.
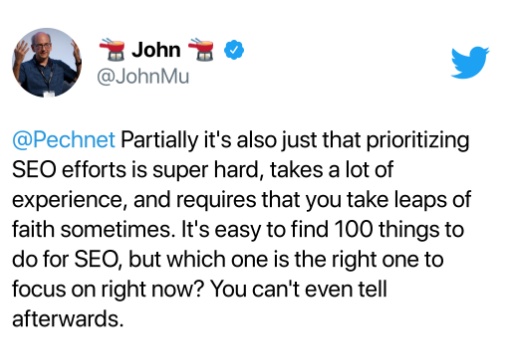
He’s right, of course. We don’t know exactly which of the things that we told you to do worked, and in truth, it’s got to be combinations of things, but this is your regular warning that anyone telling you they have the secrets is not being honest.
Here is another secret. We have an incredibly active industry that constantly shares case studies and information. That’s what Canadian SEO Joy Hawkins did last week with this fantastic overview of Florida law firms that showed how their search visibility changed after a big Google update several weeks ago. They’ve dubbed the update the “Vicinity Update” based on the change in rankings for those firms shown in close proximity to the searcher.
4. Spotlight Explainer — Log4j Vulnerability
About one-quarter of computer servers use software called Apache, a twenty-five year old open source platform offered for free to everyone. One of its most popular logging tools used for analytics is software called Log4j. Hackers have devised a way to break into servers using that code.
Sizing the Log4j vulnerability problem
Jen Easterly is the U.S. Director of the Cybersecurity and Infrastructure Agency. She’s a West Point graduate, a Rhodes scholar, a twenty year combat vet with two Bronze Stars, has worked at the NSA, was Morgan Stanley’s global head of cybersecurity, and came back to the federal government to lead CISA.
She told industry leaders that the Log4j vulnerability “is one of the most serious I’ve seen in my entire career, if not the most serious.”
Everything from ransomware to denial of service attacks is open to hackers on unpatched servers.
Ubiquity makes this a big deal
CISA estimates that hundreds of millions of devices globally are at risk. And because of the nature of computer servers, they can potentially affect many others.
Companies known to be involved with mitigation efforts for more than one week: Oracle, Microsoft, Amazon, Google, Cisco, RedHat, and more.
It’s not as easy as upgrading your computer
There really isn’t an apt comparison for someone who isn’t a cybersecurity professional. There was a fix for this problem, but last Tuesday, researchers at Akamai discovered that the fix could be bypassed. Apache published another fix late Friday, and here we are on Monday, but that’s not enough time for any organization to have potential problems fixed.
One of Easterly’s executives addressed the issue this way: “There’s no single action that fixes this issue. It’s a mistake to think anyone is going to be done with this in a week or two.”
What next? CISA is updating a page on their site throughout the crisis and has told the cybersecurity world to “update or isolate affected assets. Assume compromise, and hunt for signs of malicious activity.”
5. Did That Really Happen? — Why Covid-19 Testers Don’t Have to Quarantine
The CDC has done more than its share of fact checking over the last two years, and now faces a series of dumb posts alleging that testing personnel don’t have to isolate when coming in contact with someone who tests positive for COVID-19.
The inaccurate meme has been shared more than 50,000 times and generated a lot of buzz. The reason why they don’t, according to the scientists, has to do with the presence of medical PPE and the amount of exposure. CDC guidelines only call for quarantine if someone has been closer than 6 feet from an infected person for 15 minutes or more.
6. Following Up — NSO Group
Back in July we told you about NSO Group, an Israeli spyware company whose software was found planted on thousands of phones belonging to journalists, activists, and fourteen heads of state. Amazon kicked the company off its servers, and Apple sued them.
Google’s Cybersecurity group has researched the exploit and published a report last week that said the software was one of the most technically sophisticated they had ever seen and rivaled software thought to be accessible to only a handful of nation states.
The plum quote picked out by Cyberscoop’s excellent coverage: “Short of not using a device, there is no way to prevent exploitation … it’s a weapon against which there is no defense.”
7. Protip — What Data Can You Share?
This is the season for infographics synthesizing data at your house, organizations, or businesses. If you were born in a year that begins with a “1”, you can remember a time when technologists talked about “big data”.
The great news is that big data is here, and you can use it. Think about how Spotify Wrapped uses a simple report dressed up as a playlist to generate millions of impressions. Or take a look at these graphics from Instacart that show the hottest grocery store products tied to popular recipes this year.
Protip: have fun doing it. Instacart measured the number of bananas ordered in LA as able to create a stack as high as 87,196 Hollywood signs.
8. Screening Room — Chevy Tearjerker
9. Science Fiction World — Remotely Powering Drone Flight
DARPA (those nice government types who brought us the internet) has given a grant to Electric Sky, a company that says they can use radio waves tied only to specific drones to improve on microwaves or lasers that power drones in flight.
10. Coffee Break — The Best of Primitive 1990s Sites
There is no way that I will show you the images from a website I built in the 1990s with a purple and pink color scheme. Decades later I remember my graphics-oriented buddy and her pained expression as she scurried away while muttering, “I must fix this.”
But Lifehacker has unearthed a bunch of 1990s era websites still live online. You’ll be able to check out the Dole-Kemp 1996 site, the Jurassic Park and Space Jam promo sites, and SFSU’s FogCam, which still provides live images of the campus 27 years later.
11. Sign of the Times
Many of you have written and said that you love our weekly Sign of the Times feature. Thanks! Remember that you can (and should!) write me whenever you want–just press reply.
Until we see you again on January 3, we assembled a photo album of all of the signs we posted this year. Enjoy it, stay safe, and wear your mask.
